Introduction
In the traditional financial services industry, third-party service providers such as custodians, exchanges and fund administrators leverage SOC (System and Organization Controls) reports to build stakeholder trust and confidence. SOC reports are internal control evaluations conducted by independent auditors.
The interest in attaining SOC reports has been driven by the recognition that the reports disclose important information about third-party provider controls that end-users need to comprehensively assess and address the risks of outsourced core services. Thus, the adoption of the universal SOC reporting standard by digital asset service providers speaks to the industry’s maturation and belief in providing stronger and more standardized assurances and transparency to stakeholders.
Independent audit firms (known as service auditors) perform SOC examinations on companies (service organizations) based on guidelines established by the American Institute of Certified Public Accountants
(AICPA). SOC examinations are tests of internal controls and processes that impact an organization’s end users. AICPA’s SOC reporting framework presents three reporting options. The types of services and systems a company offers along with user-specific needs informs the type and scope of audit an organization should obtain. In this piece, we explain the differences between the main reports, and how these reports apply to digital asset service providers.
Terminology
The following are key terms in the context of SOC (System and Organization Controls) reports.
Service organization: A service organization is the subject of a SOC report. It is a company to which customers outsource critical services. Exchanges, custodians, cloud providers and software-as-a-service companies (e.g. AWS) are common examples of service organizations. We use service organization and service provider interchangeably in this piece.
Service auditor: An independent CPA firm that conducts analysis and testing to assess the reliability of a service organization’s systems. Service auditors develop opinions on the service organization’s design of internal controls (provided in Type I and Type II reports) and the operating effectiveness of internal controls in meeting the objectives (provided in a Type II report) based on this testing and analysis.
User entity: A user entity is the customer or client of a service organization that seeks assurances about its service organizations. User entities request SOC reports from their service organizations. We use client, customer, and user entity interchangeably in this piece.
Control objective: A control objective articulates the aim or purpose of a specified set of processes at a service organization. Control objectives should be relevant to services offered to customers.
Controls: Controls are internal activities performed by a service organization; an auditor evaluates a set of controls to determine if the respective control objective has been met.
Trust services categories: Trust service categories are areas of focus in SOC 2 reports. The five categories are security, availability, processing integrity, confidentiality and privacy. A SOC 2 report may
include multiple categories.
Trust services criteria: Evaluation criteria that can be used to determine the suitability of the design of a service provider’s systems and the operating effectiveness of controls relevant to the trust services category being assesses.
SSAE 18: Standards developed by the AICPA for use by service auditors against which to evaluate internal controls at service organizations.
AT Section 320: This is a sub-section of SSAE 18 that is relevant to SOC 1 reports.
AT Section 105: This is a sub-section of SSAE 18 that is relevant to SOC 2 and 3 reports.
AT Section 205: This is a sub-section of SSAE 18 that is relevant to SOC 2 and 3 reports.
The Emergence of SOC Reports
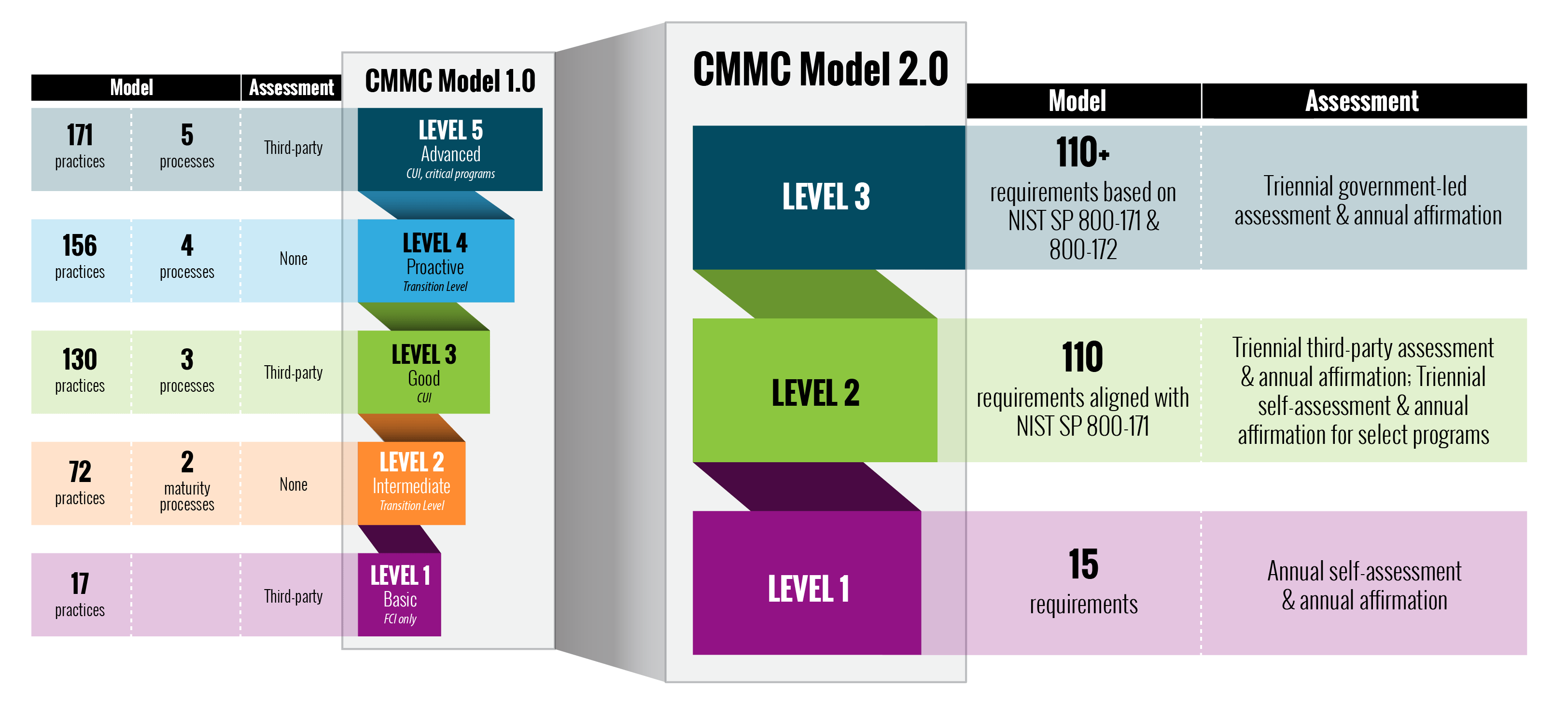
The growth in outsourcing critical financial and IT functions to specialized organizations has fueled the development of the standardized SOC system for evaluating internal controls. The AICPA introduced the SOC reporting framework in 2011 to refresh older standards (specifically SAS 70) and expand the subject matter covered by internal control audits.
The updated SOC framework provides standardized audit options to the evolving landscape of service organizations and reconciles with international accounting standards (specifically, ISAE 3402). The updated framework consists of SOC 1, SOC 2 and SOC 3 reports that are prepared in accordance with sub-sections of the AICPA’s audit standards, known as the Statement on Standards for Attestation Engagements No. 18 (SSAE 18).
SOC 1 reports broadly comment on controls and processes that impact user entity financial statements and reporting.
SOC 2 reports comment on controls and processes that address the security, availability and/or processing integrity of systems and/or confidentiality, privacy data.
SOC 3 reports are condensed, less detailed version of a SOC 2 report.
Report Requirements
While service organizations are generally not required by law to undergo SOC audits, one of the main reasons for enlisting an audit firm to issue a SOC report is that user entities are increasingly demanding such internal control reports from their outsourced-service providers. One way this has manifested is via contractual terms between a service organization and its clients that require the service organization to engage independent auditors regularly to conduct SOC audits.
Type I vs Type II
SOC 1 and 2 reports can be sub-categorized into Type I and Type II reports.
Type I report is an attestation of controls at a service organization at a specific point in time and contains the auditor’s opinion on the fairness of the design of internal controls.
Type II report is an attestation of controls at a service organization over a minimum six-month period and generally more comprehensive as they incrementally include the auditor’s opinion on the operating effectiveness of the controls over the audit period and a detailed account of the tests the auditor performed and the results of the tests.
Report Components
In SOC 1 and SOC 2 Type I reports, the service auditor outlines the scope of the audit, the responsibilities of the service organization and auditor in the audit process and an opinion on the design of the system and controls at a specific point in time. In SOC 1 and SOC 2 Type II reports, the service auditor outlines the scope of the audit, the responsibilities of the service organization and auditor in the audit process, the limitations of the audit, the outcome of the tests, the provider’s effectiveness in achieving the objectives and the auditor’s final opinion based on the results of the tests.
| SOC 1 | SOC 2 Type I |
| Auditors opinion | Auditors opinion |
| Managemant assertion | Managemant assertion |
| Description of system and controls | Description of system and controls |
| Control objectives | Trust services categories and criteria |
| Auditor’s tests of controls* | Auditor’s tests of controls* |
| Auditor’s results of tests* | Auditor’s results of tests* |
| Other information | Other information |
Typical SOC Engagement
There are four distinct phases in an initial SOC engagement:
- the initial conversation between firm and auditor
- readiness assessment
- remediation
- reporting
In the initial conversation, auditor and service providers determine the appropriate report and scope. The service auditor then performs a readiness assessment to identify areas that require attention and remediation in advance of the audit. The following remediation period gives the organization a chance to address any potential gaps highlighted by the auditor. The audit ensues. A service organization will usually engage an auditor to produce a Type I report before the deeper Type II engagement.
SOC 1® Report
Reporting on Controls at a Service Organization Relevant to User Entities’ Internal Control over Financial Reporting
This meets the needs of user entities’ managements and auditors as they evaluate the effect of a service organization’s controls on a user entity’s financial statement assertions. These reports are important components of user entities’ evaluation of their internal controls over financial reporting for purposes of compliance with laws and regulations and for when user entity auditors plan and perform financial statement audits.
SOC 2® Report
Reporting on Controls at a Service Organization Relevant to Security, Availability, Processing Integrity, Confidentiality, or Privacy (SOC 2)
For those who need to understand internal control at a service organization as it relates to security, availability, processing integrity, confidentiality or privacy. These reports can play an important role in oversight of the organization, vendor management programs, internal corporate governance and risk management processes, and regulatory oversight. Stakeholders who may use these reports include management or those charged with governance of the user entities and of the service organization, customers, regulators, business partners and suppliers, among others.
SOC 3® Report
Trust Services Principles, Criteria, and Illustrations
Designed to accommodate users who want assurance on a service organization’s controls related to security, availability, processing integrity, confidentiality or privacy but do not have the need for the detailed and comprehensive SOC 2® Report. It can be used in a service organization’s marketing efforts.
SOC Report Comparison
| Report | Audience | What | Why |
| SOC 1 | Users’ controller’s office and user auditor | Controls relevant to user financial reporting | Audits of f/s |
| SOC 2 | Management Regulators Others | Concerns regarding security, availability, processing integrity, confidentiality or privacy | GRC programs Oversight Due diligence |
| SOC 3 | Any users with need for confidence in service organization’s controls | Easy-to-read report on controls | Marketing purposes; detail not needed |
Which SOC Report is right for you?
| Will report be used by your customers and their auditors to plan/perform an audit of their financial statements? | Yes | SOC 1 |
| Will report be used by customers/stakeholders to gain confidence and place trust in a service organization’s system? | Yes | SOC 2 or SOC 3 |
| Do you need to make report generally available? | Yes | SOC 3 |
SOC 3® over SOC 2® Reports
Do your customers have the need for/ability to understand the
details of processing and controls at a service organization, the tests performed by the service auditor and results of those tests?
If Yes, SOC 2®. If No, SOC 3®.