On December 26, 2023, the Department of Defense (DoD) published for comment a proposed rule for the Cybersecurity Maturity Model Certification (CMMC) 2.0 program, a revamped version of from the History of Cybersecurity Maturity Model Certification (CMMC). The new regulation, outlined in a proposed rule change to the Defense Federal Acquisition Regulation (DFARs), seeks to reduce the burden on contractors by paring down cybersecurity requirements.
You have already reviewed How to Prepare for CMMC and now want to understand the implementation details of CMMC 2.0.
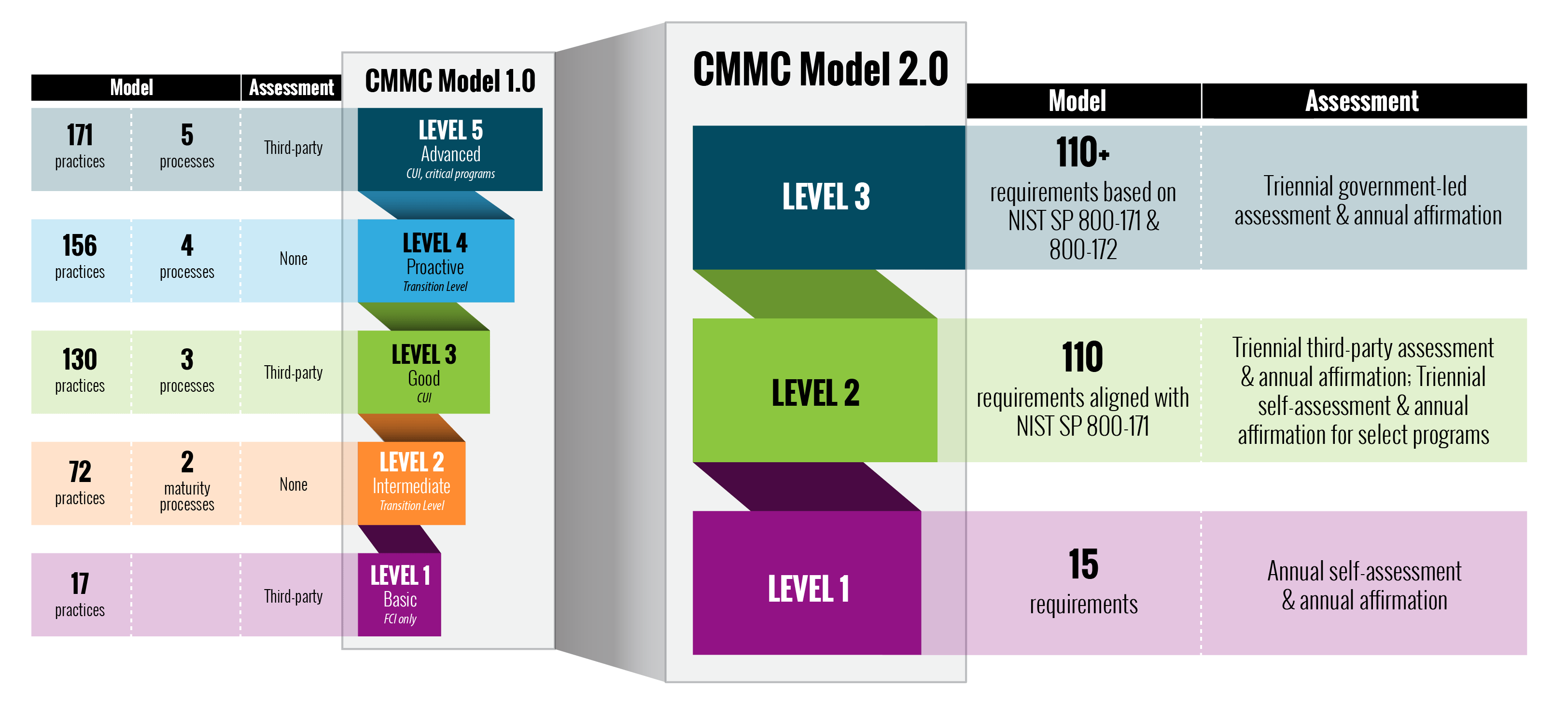
Changes in Scope and Complexity
CMMC 2.0 reduces the number of security tiers from 5 to 3.
Self-assessment for non-prioritized acquisitions not critical to national security.
Third-Party Assessment for prioritized acquisition critical to national security.
CMMC 2.0 Level 2 (Advanced) will be aligned with NIST 800-171
CMMC 2.0 Level 3 (Expert) will be aligned with NIST 800-172
CMMC 2.0 will have limited use of POAMs.
Relationship of CMMC and NIST 800-171r2 and r3
Contractors with a DFARS 7012 clause in their contract is obligated to adhere to NIST 800-171 r2. 800-171r3 is currently in the Initial Public Draft period until January 24th, 2024, and final release is anticipated in Spring 2024 which is anticipated to bring changes to CMMC 2.0.
Currently NIST 800-171 r2 comprises 110 controls that must be fulfilled for compliance. In the case of NIST 800-171 r3, the number of controls has decreased by 15, but has increased the assessment objectives by 125 measures.
Availability of Certified Assessors
CMMC 2.0 introduces a broader waiver process for contractors, adding an extra layer of flexibility. However, the compliance ecosystem has yet to assess the impact to the potential reduction in the demand for accredited assessors given the already tight labor market for qualified professionals.
Posible False Claim Act Litigation
Any contractor who doesn’t take this new regulation seriously risks losing their DoD contracts and penalties under the False Claims Act (FCA).
In October 2021, the Department of Justice (DOJ) launched the Civil Cyber-Fraud Initiative, which further incentivized whistleblowers to identify among other things, contractors claiming to perform preventative cybersecurity practices which they in fact do not.
If a contractor violates the FCA, they can be fined up to 3x the total value of the contract and an additional s over $11k per claim. In 2019 alone, the DOJ obtained more than $3 billion in settlements and judgements stemming from false claims act violations and other fraud. In 2020, the DOJ collected over $2.2 billion in settlements. Keep in mind that whistleblowers receive between 15 and 25% of any reward under the case and are incentivized to report bad actors.